Wireless sensor networks (WSNs) have revolutionized the way data is collected and transmitted in various applications, ranging from environmental monitoring to industrial automation. However, the pervasive use of WSNs also brings forth significant challenges, particularly in ensuring network security against malicious attacks such as worm propagation.
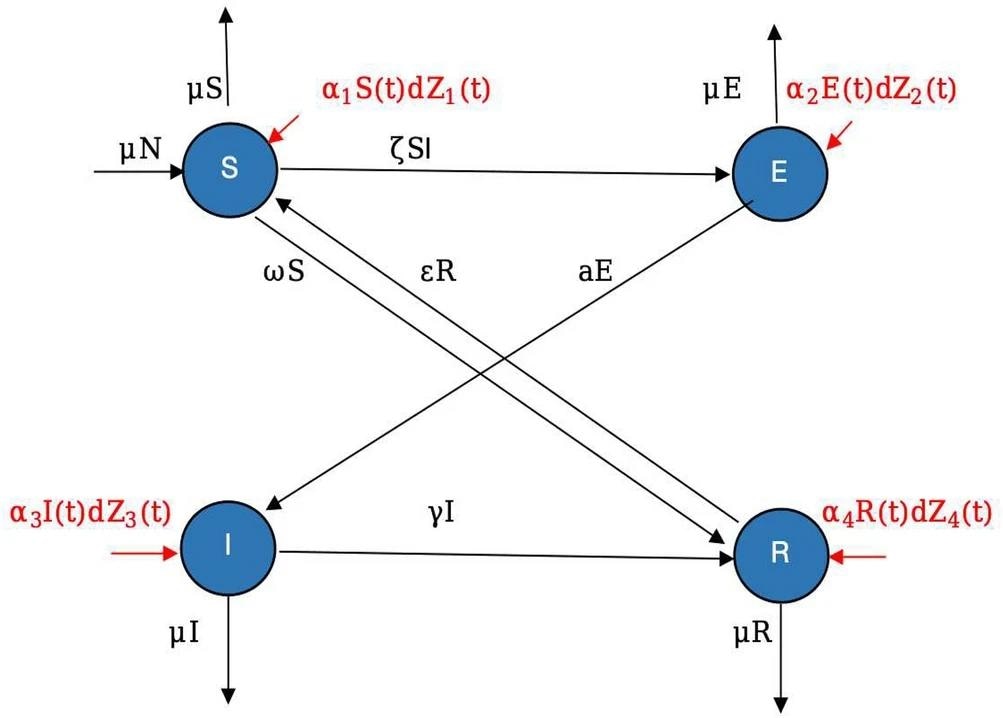 The chart shows the flow of nodes in various states of the system. Image Credit: https://www.nature.com/articles/s41598-024-59203-3
The chart shows the flow of nodes in various states of the system. Image Credit: https://www.nature.com/articles/s41598-024-59203-3
In an article recently published in the journal Scientific Reports, researchers from China have introduced a stochastic Susceptible-Exposed-Infected-Recovered-Susceptible (SEIRS) model to capture the dynamics of worm transmission in WSNs, emphasizing the impact of environmental randomness on malware propagation.
Background
Despite their widespread applications, WSNs face inherent vulnerabilities due to their decentralized architecture, resource constraints, and susceptibility to malicious attacks. Of particular concern is the threat of worm propagation, where a single infected node can rapidly disseminate malware to neighboring nodes, compromising the integrity and functionality of the entire network.
Previous research in the field of WSN security has predominantly focused on deterministic models to analyze and predict the dynamics of worm spread. While these models have provided valuable insights into the mechanisms of malware transmission, they often overlook the stochastic nature of real-world scenarios, where environmental fluctuations and parameter uncertainties play a significant role in shaping the dynamics of worm propagation.
As a result, there is a growing recognition of the need to incorporate stochastic elements into existing models to capture the complexities and uncertainties inherent in malware spread dynamics.
The Current Study
The research employed a stochastic SEIRS model to simulate worm spread in WSNs, considering factors such as node vulnerability, information dissemination, and environmental influences. The methods can be divided into the following steps:
Model Formulation: The model extends the traditional SEIRS framework by incorporating stochastic components to capture the inherent uncertainties in malware transmission dynamics. Specifically, the model considers the susceptible (S), exposed (E), infected (I), and recovered (R) states of nodes in the network, reflecting the progression of worm infection.
Environmental Randomness Integration: To account for environmental variability, Gaussian white noise was introduced into the model as a representation of stochastic influences on worm spread. This inclusion of randomness allows for a more realistic depiction of the dynamic behavior of malware propagation in WSNs, considering the impact of parameter fluctuations and environmental fluctuations on the spread of worms.
Numerical Simulations: Numerical simulations were conducted to validate the stochastic SEIRS model and assess its effectiveness in capturing the dynamics of worm transmission in WSNs. Various parameter sets were utilized to explore the behavior of the model under different scenarios, providing insights into the interplay between environmental randomness and malware propagation.
Threshold Determination: The study determines threshold values for the stochastic system, establishing a set of sufficient conditions that dictate the persistence or extinction of worm spread in WSNs based on mean behavior.
Lyapunov Function Analysis: The model's globalized, positive, and feasible nature was assessed through the application of Lyapunov function analysis, ensuring the stability and reliability of the stochastic SEIRS framework. This analysis provided a theoretical foundation for understanding the behavior of the model and its implications for worm spread dynamics in WSNs.
Ergodic Stationary Distribution Analysis: The study establishes sufficient conditions for the existence of an ergodic stationary distribution in the stochastic SEIRS model, elucidating the long-term behavior of worm spread in WSNs. By analyzing the stationary distribution, the research offers insights into the equilibrium states of the system and the persistence of malware transmission over time.
Qualitative and Quantitative Verification: The results obtained from the model were qualitatively and quantitatively verified through numerical simulations, demonstrating the accuracy and reliability of the stochastic SEIRS framework in capturing the dynamics of worm propagation in WSNs. By validating the model against empirical data and theoretical analyses, the study confirmed the effectiveness of the proposed approach in enhancing our understanding of malware transmission dynamics.
Results and Discussion
The study uncovers the pivotal role of environmental randomness in shaping worm transmission dynamics within WSNs. Through the identification of threshold values and the establishment of sufficient conditions, researchers unveil the determinants of worm spread persistence or extinction, shedding light on factors influencing malware propagation in networked environments.
This study underscores that implementing effective control strategies can significantly mitigate worm spread, highlighting the importance of proactive measures in enhancing network security.
Conclusion
In summary, the research presents a comprehensive analysis of stochastic worm spread in wireless sensor networks, offering valuable insights into the dynamics of malware transmission in complex networked systems.
By integrating environmental randomness and incorporating stochastic elements into the SEIRS model, this study offers a nuanced understanding of worm propagation dynamics. The findings highlight the significance of proactive control measures in containing worm spread and fortifying network resilience against malware attacks.
Journal Reference
Liu, P., Din, A. (2024). Comprehensive analysis of a stochastic wireless sensor network motivated by Black-Karasinski process. Scientific Reports 14, 8799. https://doi.org/10.1038/s41598-024-59203-3, https://www.nature.com/articles/s41598-024-59203-3