Apr 6 2010
The DefensePro 5.0, which safeguards networks against cybercriminal attacks, has won the 2010 Global Product Excellence in Intrusion Detection and Prevention Solution – Customer Trust Award.
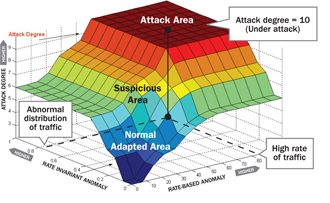 Radware Defensive Proadaptive Intelligence Engine
Radware Defensive Proadaptive Intelligence Engine
The customer trust honor endorses the reality that the DefensePro 5.0 leads the curve in relation to the top category products that are able to offer the best security for intrusion detection and prevention. The leading information security research and advisory guide in the industry, the Info Security Products Guide, has named Radware’s DefensePro 5.0 for the award. Radware is the principal vendor who offers integrated delivery solutions to the business-smart networking domain.
The award is declared on the basis of worldwide voting by customers who indicate their favorite information security solutions that are judged on the basis of dependability, ability to safeguard against unauthorized intrusion, and performance.
The DefensePro 5.0 is an integral constituent of the Business-Smart Data Center strategy of Radware. DefensePro is based on a methodology that provides many innovative capabilities. It also provides a range of useful on-demand platforms and pay-as-you-grow oriented procurement models.
The DefensePro 5.0 is an improved version of Radware’s winning intrusion prevention system (IPS). The award-winning IPS is designed to safeguard application infrastructure from emerging non-vulnerability and zero minute network threats, as well as cybersecurity attacks. This security solution mitigates DDoS attacks for a maximum extent of 10 million packets-per-second (PPS). The solution processes genuine traffic and also eliminates hazards of bypassing the security engine and avoids blocking the authorized users during the mitigation process.
Avi Chesla, Radware’s Vice President Security Products, informed that the DefensePro is designed to decrease network vulnerability and thwart harmful cyber attacks.