Oct 16 2012
Potentially vulnerable industrial control systems today got a big boost in security with the publication of a new specification from the Trusted Computing Group (TCG) that adds additional layers of security to standard shared network infrastructure. Such security will protect critical energy, utility, healthcare and manufacturing systems that have been increasingly targeted for attacks.
 Trusted Computing Group's IF-MAP Metadata for ICS Security specification will help improve security for vulnerable industrial control systems. (Graphic: Business Wire)
Trusted Computing Group's IF-MAP Metadata for ICS Security specification will help improve security for vulnerable industrial control systems. (Graphic: Business Wire)
The specification will be introduced at this week’s Industrial Control Systems Joint Working Group (ICSJWG) 2012 Fall Meeting during a two-hour panel session on “Public Standards for Interoperable ICS Security,” led by Steven Venema of The Boeing Company (a TCG member company).
A 2011 NIST report on the topic of industrial control systems security notes that integration of traditional ICS systems - such as supervisory control and data acquisition (SCADA) systems, sensors, actuators, and controllers - with IT networks has opened these networks to external threats, and the problem is exacerbated by the growing use of wireless connectivity.
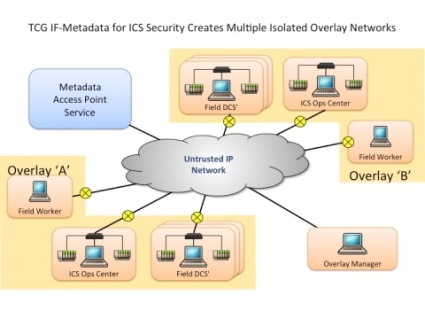
The TCG IF-MAP Metadata for ICS Security specification facilitates the deployment, management, and protection of large-scale industrial control systems by enabling creation of secure virtual layer 2 and/or layer 3 overlay networks on top of standard shared IP network infrastructure typically used in industrial control systems. Overlay networks isolate key components of these systems into protected enclaves.
The TCG specification builds on the soon-to-be-published ISA100.15 architectural model for secure ICS communications over untrusted shared networks (TR100.15.1, “Wireless Backhaul”), which contains a new architectural model, use cases, and functional requirements such as identity-based access policy, device identification, and certificate lifecycle management.
The TCG specification follows this ISA100 architecture and is intended for use in retrofitting existing industrial control systems, as well as incorporation directly into new ICS products, as an additional interoperable security capability.
For additional security, the TCG specification recommends IP networks support other TCG standards, including the Trusted Network Connect client functionality and the Trusted Platform Module (TPM) for remote attestation, but it can be used without those elements.
“The IF-MAP Metadata for ICS Security specification is a generational leap forward for adding secure connectivity to industrial automation devices,” said David Mattes, TCG invited expert and founder and CTO of Asguard Networks. “The philosophy and contents of this specification are guided by seven years of development and deployment experiences in a global manufacturing environment. Asguard Networks is implementing this specification as part of our SimpleConnect™ product line to make the full lifecycle management of segmented overlay networks easy and efficient, at both small and large scales."